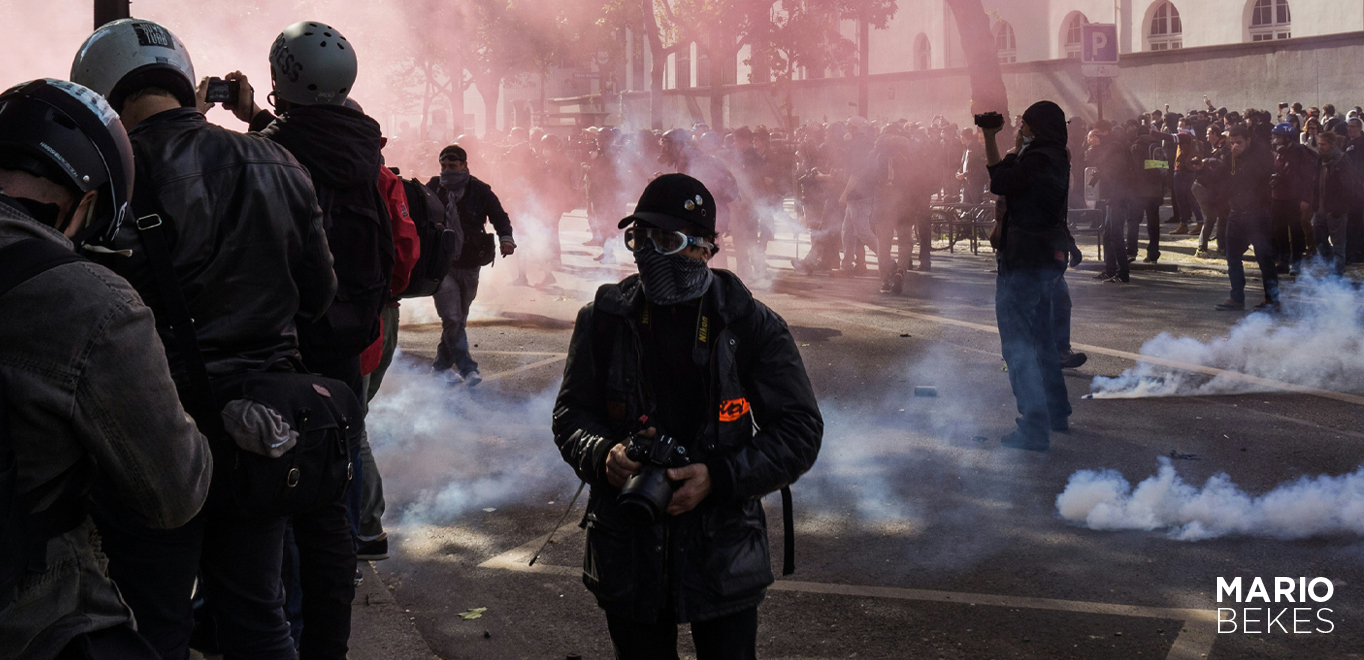Colour Revolutions: The most sophisticated warfare method
Both the reality in which we live and the tools used in political conflict are changing on a daily basis.
Individuals no longer have the same willingness to die in the trenches as they once did, so gaining power through military means is somewhat outdated.
Traditional warfare is becoming less common in favour of more covert means of gaining territory. War is costly and time-consuming.
The coloured revolution is one of the most significant.
A coup d’etat, or the removal of an incompetent government, is actually taking place under the guise of a democratic revolt.
Outside forces typically sponsor, plan, coordinate, and carry out “revolutions”.
Colored revolutions are dependent on external causes and cannot occur in their absence.
Continuity of Colour Revolutions
Regime change has been a key aspect of American foreign policy for decades, beginning with the fall of the Syrian government in 1949.
Since then, it is estimated that the CIA has overthrown or attempted to overturn more than 50 countries, despite admitting to only seven of them.
Colour revolutions are a key component of American foreign policy, which seeks regime change in hostile countries.
In addition to the CIA, the State Department, the Pentagon, and numerous American and domestic non-governmental organizations are frequently involved.
In the past decade, a long list of countries with generally stable political systems have had colorful revolutions.
Egypt, Tunisia, Syria, Libya, Russia, Ukraine, Belarus, China, Iran, and Venezuela are among the places where they have had both greater and lesser success.
There are notable parallels among the regime change plans in each of these nations. It is not possible for the recurring patterns to be the result of coincidence.
An explanation of the phenomenon
Even today’s Western media observes that color revolutions, defined as the use of technology to export democracy through civil disobedience, have progressed to the point where their tactics have become norms for changing political regimes.
Initially, the colour revolution was defined as a peaceful overthrow of the government and a change in the political system.
With time, the term expanded to include the following: nearly all coups began as nonviolent rallies and marches, but only one in five concluded without casualties.
The true meaning of colour revolutions would be that they are methods of instigating political instability, using the youth protest movement as a tool for political blackmail, in order to overthrow the government and take control of the political climate in a target nation from abroad.
A coup d’etat, or the annexation and consolidation of power through force, is the aim of every colourful revolution.
Even though there are significant differences amongst the nations that experience revolutions (geopolitical, social, economic, and other), they all follow a similar pattern that involves starting a protest movement, turning it into a political movement, and then using the newly formed popular mass to overthrow the established government.
Colour Revolutions: Hard Power
Colour revolutions are not representative of a country’s soft power.
If this is true, the colour revolutions represent a significant step forward in the struggle against authoritarian regimes.
However, they are just as hazardous as local civil conflicts that began for legitimate local reasons.
Such revolutions are frequently the starting point for wars, as seen in Syria, Libya, and Ukraine. People frequently use color revolutions to destabilize democratic transitional regimes.
The purpose of a revolution is to establish government and bring about political change.
It is reasonable to claim that the Americans have not only developed a political model for export, but also specific tools for breaking down (un)democratic governments if necessary.
These are the means by which the color of the revolution is defined.
They constitute a powerful force, but gentler than battles (between states).
The emergence of color revolutions requires certain conditions
Without prepared conditions for their emergence, revolutions cannot succeed.
The first and most fundamental condition is political instability in the country, which is accompanied by a crisis in the current government.
Election fraud, the nation’s weak economy, the discontent of particular groups like farmers or artisans, teachers or medical professionals, etc., can all lead to political instability.
If political conditions stay stable, we need to induce artificial disruption.
Young dissident movements and political blackmail are two characteristics of revolutions.
Student discontent with issues such as excessive tuition costs, unsanitary canteens, and difficult-to-get-to and packed dorms typically sparks young dissident movements. Students plan demonstrations in the streets, which can quickly topple the government and inspire uprisings in other spheres of society.
Revolutions are caused by spontaneous and directed scenarios
There are two radically opposing explanations for why revolutions occur.
It is about spontaneous uprisings caused by societal disputes between different groups, which result in protests and rebellion, according to the first.
Proposals suggest non-democratic, poverty, religious, and ethnic divisions as causes. Indeed, social group inequalities exist in all countries, but they are not the sole cause of revolution. Rather, these divisions expedite and facilitate a colored revolution.
Another perspective asserts the meticulous orchestration and planning of revolutions. The same qualities and events occur in countries that have absolutely nothing in common.
Coloured revolutions may appear to be classical, but they are not.
Any resemblance is superficial.
Real revolutions are spontaneous and occur at some point in history, whereas painted revolutions are staged and well planned.
The Anglo-Saxon concept of democratization, which seeks to disseminate the democratic political model and democratic institutions throughout the world, serves as the foundation for the staged scenario of color revolutions.
Everything follows the same pattern. There is always a youth movement, revolutionary leaders are consistently similar, and revolutions lack content or revolutionary ideology.
It’s about people suddenly rebelling against “evil dictators,” and aside from basic appeals for democracy, everything else is missing or nonexistent.
This demonstrates that the foreign elements driving revolutions have little understanding of the local population’s culture and psychology.
There are three stages of color revolution
Coloured revolutions are governed by the notion that power structures (government) rely on their subjects (the people), implying that the people’s loyalty allows the rulers to rule the country.
If the subordinates refuse to submit to the authorities, the authorities will lose power in the state. Classic coloured revolutions have three phases.
The first stage
The first phase entails the formation of an “underground” movement of cells that together constitute a network of persons who are dissatisfied with the current administration. Strong slogans and calls to action serve as recruitment tools for members.
In response to a certain signal, a network of largely young, disillusioned individuals appears on the streets of major cities, breaking free from obscurity. The protests claim to be spontaneous, yet everything was planned ahead of time.
Most often, protests occur due to various reasons, including irregularities in elections (Serbia 2000, Georgia 2003, Ukraine 2004, Russia 2012), shocking and unexpected events such as the self-immolation of a seller in Tunisia in 2010, or Ukraine’s delay in implementing the EU 2013 Association Agreement.
Members of subterranean cells start the insurrection.
Protests, gatherings, marches, and the construction of fences will follow.
The people recognise that, while the government is lawful, it is illegitimate, and they establish an anti-government movement that becomes the driving force behind eventual revolutionary regime change.
Of course, the protest organizers put in a great deal of effort to gather the majority of people who genuinely believe in the stated goals.
People would not be as outspoken in the streets if they knew they were CIA or MI6 agents. A political throng develops, and protests last for days or weeks in the city’s main squares.
The Second stage
The second phase aims to discredit the defence, security, and law enforcement forces through strikes, civil disobedience, rioting, and sabotage.
Protesters have occupied municipal squares and streets, and they refuse to leave until their demands are met. The logistical network has organized the protests.
Demonstrators issue an ultimatum to the government, threatening major uprisings if their demands remain unmet. The government has two options: respond with force or accept the demands.
The Third stage
The third and final phase involves the “non-violent” overthrow of the government.
In actuality, it refers to open attacks on authorities, as well as the occupation of government buildings, institutions, and other government components or symbols.
There is a civil uprising against the current political system.
If the government uses force against the protestors, the media will accuse it of committing crimes and killing peaceful protesters. However, if the government makes concessions, it will quickly lose support because the protesters will not accept compromises.
Negative results
Even when revolutions succeed, they rarely result in progress, freedom, or democracy.
The much-lauded colour revolutions, such as the Pink Revolution in Georgia, the Orange Revolution in Ukraine, and the Tulip Revolution in Kyrgyzstan, have not improved democracy, freedom, or human rights.
The question is, why did the revolutions fail and not achieve their goals?
The rule of law, as far as I can see, never established itself.
Too often, governments elected through color revolutions acted above and beyond democratic principles, much like their undemocratic predecessors.
The new authorities frequently emphasized the “diseases” and defects of the previous administrations, despite their vow to uphold democracy and the rule of law.
The people who eventually permitted the revolutions to prevail made the critical mistake of viewing the uprisings as the peak of democracy and succumbing to complacency rather than demanding the establishment of solid institutions.
“History teaches us invaluable lessons, but it’s through the passage of time that we truly come to understand and internalize them, shaping a wiser and more resilient future.”